Catching the scammer through cryocurrency tracking.
OSINT & CRYOCURRENCY.
Original text and other information on OSINT is available at>>>>
( https://www.advisor-bm.com/advisorbm-news )

His nostrils were permanently flared, as though he sniffed invisible winds of art and commerce. William Gibson, "Count Zero"OSINT & CRYOCURRENCY.
Original text and other information on OSINT is available at>>>>
( https://www.advisor-bm.com/advisorbm-news )

In this article I will show:
How, using the basics of financial investigation and OSINT, we can prove the affiliation of cryocurrency addresses
How by analyzing the transactions of two or more ETH addresses, we can aggregate them into a cluster (i.e. multiple addresses controlled by the same entity)
How the attacker's economic activity dataset changes once the addresses are clustered together
Let's get started!
The most popular onchain detective ZachXBT once posted the following tweet
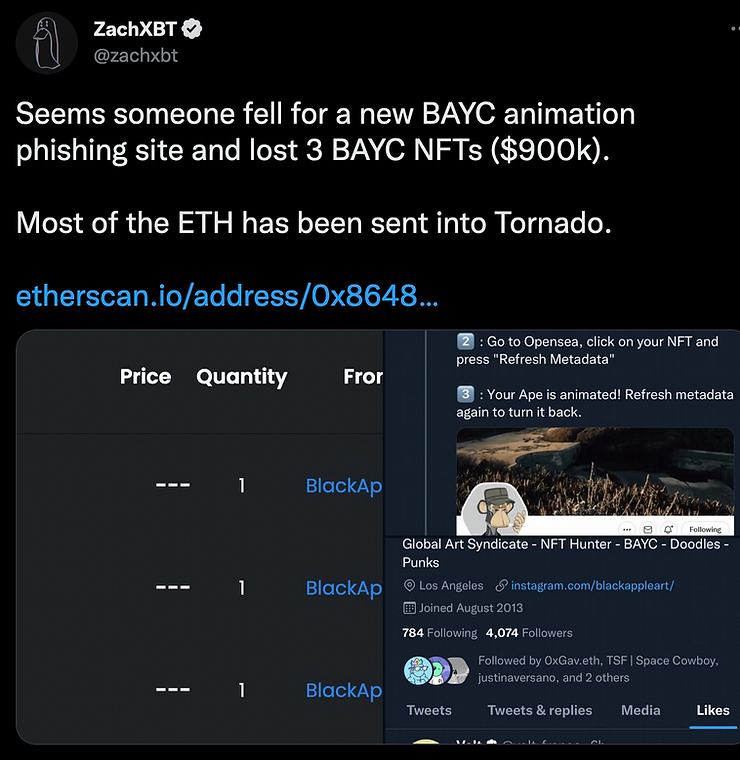
For those unfamiliar with English, let me explain. Using a phishing site, a hacker gained access to the victim's address and stole 3 ERC-721 tokens (NFT). Immediately after the theft (i.e. after sending the tokens from the victim's address to his address, 0x864875aef79B107221bEE89C8ff393BD2B666d96) the hacker sold the NFT on the marketplace Opensea.io. The criminal profits were then laundered through the Tornado.Cash mixer.
While our hands are itching to get the target address into https://etherscan.io sooner rather than later, we'll stop on the shore and turn to the theory. The criminal first stole and then sold tokens that use the Ethereum blockchain infrastructure.
In order to operate the tokens, you need some amount of cryocurrency to pay transaction fees. In our case it is the Ethereum blockchain, which means you need some ETH to send tokens or sell them.
Let's try to find out where the hacker's address 0x8648... ETH he needed to pay commissions came from.
This line of enquiry is called a source search
Open Etherscan, insert the address, see the first transactions. They will be right at the bottom of the page.
And here are the ones we need: 1, 2. The sender of the funds in the transaction table is always shown on the left of the IN (incoming transaction) or OUT (outgoing transaction) bar

So, we have identified the source of the funds, which is address 0xA474cE48300D91334339fb5aDeF99A1B11B1cfe6. What can we extract from this information?
In our case, the first address of the hacker, 0x8648... (aka Fake_Phishing5435 in the picture above) never received any funds before the transactions we detected. So address 0xa474... is the sponsor address (or funding address) with respect to the hacker address, or 0x8648..., or Fake_Phishing5435.
Most often the sponsor address is affiliated with a target address. The owner of the sponsor address could be, for example, some customer who has paid for services with cryo. Or, for example, the sponsor address is operated by a cryocurrency exchange whose services are used by the owner of the target address.
But even more often, both the target address and the sponsor address have the same owner. Let's analyze the transactions of the sponsor address and try to figure out which oion would be correct in our case.
The most interesting direction in the case of the sponsoring address is to try to detect suspicious transactions (such as the theft of NFT). To do this, open the address in Etherscan.io and go to "ERC-721 token Txns", which is the section responsible for NFT transfers.
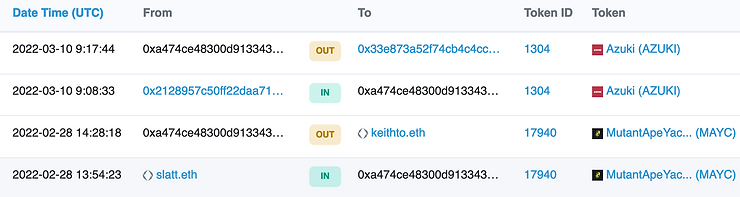
We see four transactions, two incoming, two outgoing. The first NFT, Mutant Ape Yacht Club (MAYC), was sold half an hour after recei. The second, Azuki, 9 (!) minutes later. Seems suspicious to me!
But how do we prove that these transactions are not a normal sale, but a real theft? By the consequences!
In order to sell MAYC, you have to contact the Opensea marketplace's smart contracts. When you interact with them, the marketplace will automatically generate a profile for you, accessible via a link like "https://opensea.io/ETH_Address".
I should also add that Opensea.io actively cooperates with law enforcers and also actively assists victims. In case of hacking, the stolen tokens are blocked and the hacker's account is banned, making his profile inaccessible.
Let's try to open the profile of address 0xa474... and examine the transaction history. To do so, go to https://opensea.io/0xA474cE48300D91334339fb5aDeF99A1B11B1cfe6.

oops! the address was banned.......
We now know two facts about the sponsor address: it transferred money to the hacker's address, which was then used as a commission, and also made questionable transactions with NFT, for which it was banned from Opensea.io.
The target address also made questionable transactions with NFT and was banned from Opensea.io.
Now let's find out where the criminally obtained coins were sent to. To do this, let's examine the transactions in chronological order and try to find the incoming transactions immediately after the sale of (possibly) stolen NFTs. In this way, we will determine the amount of criminally acquired funds.
The transactions we are looking for are found in the Internal Txns section:

The hacker received a total of 23.8 ETH. To do this, let's examine the transactions in chronological form and try to find the incoming transactions immediately after the sale of (possibly) stolen NFTs. Who else sent the stolen coins to address 0x945b...? Target address!

Withdrawal transactions of stolen funds highlighted in yellow
Let's find out what address 0x945b was used for... To do that, we again study the transactions in chronological order, we are interested in all incoming and outgoing transactions after the address received the stolen funds.
Target email address (13 ETH) was the first one to receive the stolen funds. Next, address 0x945b accumulated presumably stolen funds from several other addresses, including the target address. The money was then, as ZachXBT wrote, withdrawn to the Tornado.Cash mixer

The money sent to the mixer was grouped into two payments of 100 ETH, of which 125 ETH originally belonged to the target address, 13 ETH to the sponsoring address, and the remaining 62 ETH to other addresses.

It turns out that either the hacker owns all five addresses and uses 0x945b as an intermediate point before money laundering, or the owner of 0x945b is a separate criminal (money launderer) whose services are used by several criminals at the same time.
Let's briefly examine the other hacker addresses: as you can see from the graph, they too have interacted with NFT on Opensea. Let's use the old vetting method and... one of the addresses is in a ban on Opensea! The second address is not in the ban, but appears in the ZachXBT investigation. Here you can see the names and faces of our heroes, the dangerous cybercriminals.
